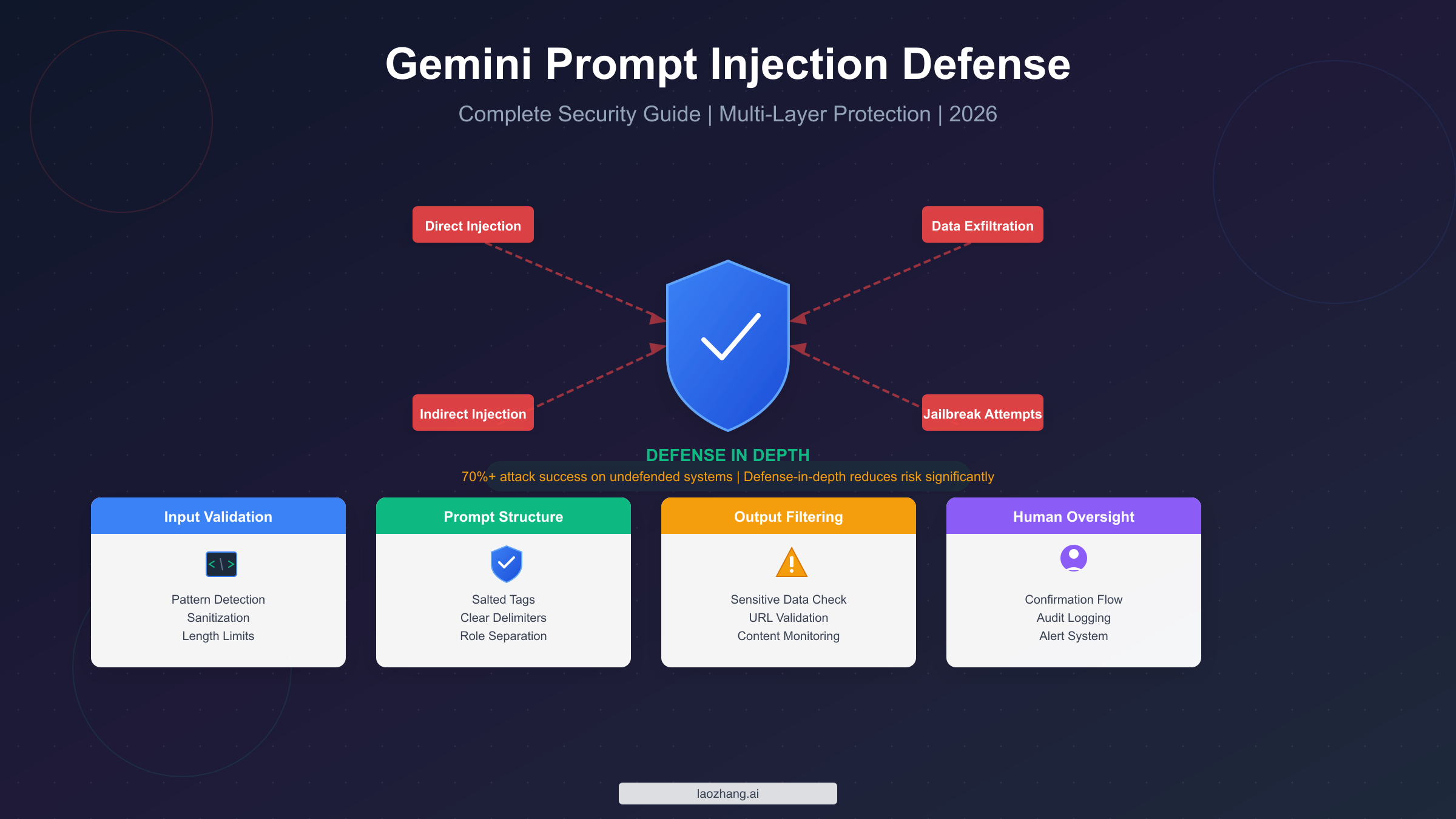
Artificial intelligence systems based on large language models are now widely used in chatbots, virtual assistants, and automated business tools. While these systems are powerful, they are also vulnerable to a growing security threat known as prompt injection. This occurs when users manipulate input prompts to bypass restrictions or force the AI to behave in unintended ways.
One of the most effective defences against this risk is strong input validation. By carefully controlling and filtering user input, organisations can significantly reduce the chances of prompt injection attacks.
Understanding the Role of Input Validation
Input validation refers to the process of checking and sanitising data before it is processed by an application. In AI systems, every user query becomes part of a prompt sent to the model. If that input is not properly controlled, malicious users may embed hidden instructions designed to trick the system.
Effective input validation helps to:
- Block harmful or manipulative commands
- Protect sensitive internal instructions
- Maintain consistent AI behaviour
- Reduce data leakage risks
- Improve overall application security
Rather than relying solely on the AI model to defend itself, validation adds an essential security layer before the prompt is even processed.
Core Techniques for Preventing Prompt Injection
Several practical validation techniques can be implemented to protect AI applications from manipulation.
1. Strict Input Filtering
One of the simplest methods is to filter out dangerous words, phrases, or patterns before they reach the model.
This can include:
- Blocking commands such as “ignore previous instructions.”
- Removing programming code snippets
- Restricting special characters or symbols
- Disallowing system-level keywords
While filtering alone is not perfect, it forms an important first line of defence.
2. Whitelisting Allowed Inputs
Instead of trying to block every harmful phrase, many systems use whitelisting. This approach only allows inputs that match predefined acceptable formats.
Examples include:
- Limiting answers to multiple-choice selections
- Allowing only specific types of questions
- Accepting structured forms instead of free text
- Restricting responses to certain topics
Whitelisting greatly reduces the opportunity for attackers to inject harmful instructions.
3. Input Length Restrictions
Prompt injection often relies on long, complex instructions hidden within user messages. Setting sensible length limits can prevent this tactic.
Practical steps include:
- Limiting the number of characters per query
- Restricting the number of lines allowed
- Truncating unusually long inputs
- Rejecting inputs that exceed defined thresholds
Shorter inputs are easier to monitor and far less likely to contain hidden manipulations.
4. Context Isolation
Another effective technique is to clearly separate user input from system instructions. This prevents the AI from confusing the two.
This can be achieved by:
- Placing user input in clearly marked sections
- Using structured templates
- Escaping special characters
- Avoiding direct merging of raw input with system prompts
Keeping instructions and user content separate makes it harder for attackers to override system rules.
Conclusion
Prompt injection is a serious and growing challenge for AI-powered systems, but it can be managed effectively with proper input validation. As AI adoption continues to expand, investing in input validation will remain a critical step in building safe and trustworthy intelligent applications.